Mobile Phone Information
Brand:
Samsung
Model:
Galaxy Note 4
Model Number:
SM-N910T
Operating System: Android 6.0.1
Application Information
Manufacturer: Synology
Inc.
Application Name: DS File
Application Version: 4.12.0-381
NAS Information
Brand:
Synology
Model: DS215j
DSM Version:
DSM 6.2.2-24922 Update 4
Forensic Imaging: Magnet AXIOM Process v3.5.1.15498
Forensic Analysis: Magnet AXIOM Examine v3.5.1.15498
SQLite Viewer:
DB Browser for SQLite (MacOS) Version 3.11.2
Summary:
DS File app for Android is
used to manage, upload, download, and share files between the NAS and the
Android device. This app requires that you have a Synology NAS running DSM 6.2
or higher.
The DS File app leaves a lot
of useful artifacts on an Android device. Articles such as databases, cache
files, and XML files all contain valuable information.
Extended:
Before we start analyzing the
data acquired, we first have to review the steps taken to stage the device.
Below were the steps taken to stage the Android device.
1.
Downloaded
and Installed DS File app from Play Store (link at the top)
2.
Logged
in with the below information
a.
Address: mobileforensics.synology.me
b.
Account: NAS_User
c.
HTTPS: Disabled
d.
Remember me: Enabled
e.
Clicking
on the gear at the bottom left will provide more settings
i. Remember IP address and account: Enabled
ii. Verify certificate: Disabled
3.
After
logging in, you will see your list of shared folders
4.
Navigated
to Data/MyTempFolder/MyFiles, selected
Synology_Security_Whitepaper.pdf
file, then selected PIN. This option
will download the file to /media/0/DSfile/PinFiles.
5.
Selected
MyTempFolder under Data, marked as a Favorite. This option will add the folder under the My Favorites tab.
6.
Opened
Synology_QuickConnect_White_Paper.pdf located
in Data/MyTempFolder/MyFiles.
7.
Emailed
Syno_UsersGuide_NASServer_enu.pdf
located in Data/MyTempFolder/MyFiles.
8.
Shared
NAS_Username_Password.docx located in
Data/MyTempFolder/MyFiles.
9.
Downloaded
Synology_NAS_Photo.pdf and QSAN_NAS_Photo.jpg located in Data/MyTempFolder/MyFiles. This will
download the file to /media/0/DSfile.
10.
Uploaded
20191111_204919.jpg located in /DCIM/Camera to Data/MyTempFolder/Uploaded Pictures.
Knowing what we’ve done on
the device will help in the analysis of this application. Now that the device
is pre-staged, we’ll use Magnet AXIOM Process to acquire a physical image, then
use Magnet AXIOM Examine to extract important artifacts. Now it’s time for
analysis!
Analysis:
Sample data can be downloaded using the link located at the top of the page.
DS File APK:
SampleData\app\com.synology.DSfile-1\base.apk
This APK is the version that
was installed on the android device.
Database File:
SampleData\data\com.synology.DSfile\databases\_download
Table: _download
This database and table
contain all files that were downloaded from the NAS using the app. The
Synology_Security_Whitepaper.pdf file that was pinned is on the list (filename
field) along with Synology_NAS_Photo.jpg and QSAN_NAS_Photo.jpg that were
downloaded. The URL field provides a URL that provides details such as the NAS
address, the path to the files, and where the file was saved to. This database
also provides the download path of where the files were saved to (download_path
field) and the status of whether the download was completed (status field).
Decoding the URLs using https://www.urldecoder.org
makes it a little easier to see what’s going on. Below is an example.
Encoded URL
http://mobileforensics.synology.me:5000/webapi/entry.cgi?path=%2FData%2FMyTempFolder%2FMyFiles%2FSynology_Security_Whitepaper.pdf&api=SYNO.FileStation.Download&method=download&mode=download&version=1&filePath=%2Fstorage%2Femulated%2F0%2FDSfile%2FPinFiles%2F1879318240.Synology_Security_Whitepaper.pdf
Decoded URL
http://mobileforensics.synology.me:5000/webapi/entry.cgi?path=/Data/MyTempFolder/MyFiles/Synology_Security_Whitepaper.pdf&api=SYNO.FileStation.Download&method=download&mode=download&version=1&filePath=/storage/emulated/0/DSfile/PinFiles/1879318240.Synology_Security_Whitepaper.pdf
Parsed URL
NAS Address:
http://mobileforensics.synology.me
NAS Port: 5000
Path to File:
/Data/MyTempFolder/MyFiles/Synology_Security_Whitepaper.pdf
Path to Save Location: /storage/emulated/0/DSfile/PinFiles/1879318240.Synology_Security_Whitepaper.pdf
Database File:
SampleData\data\com.synology.DSfile\databases\dsfile.db
Table: pinFiles_table
This database and table contain
all files that were pinned using the app. This information is redundant and is
the same information contained in the previous database (_download) but includes one additional information, last updated
timestamp. This timestamp is in epoch time and can be converted to human
readable date/time using https://www.epochconverter.com or any other epoch time converters.
Epoch time conversion:
Database File:
SampleData\data\com.synology.DSfile\databases\dsfile.db
Table: taskList_table
This database and table
contain files that were pinned (PIN), downloaded (GET), and uploaded (PUT).
This information is also redundant but provides details on whether the file was
pinned, downloaded, or uploaded.
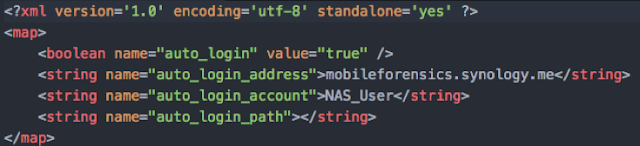
XML File: SampleData\data\com.synology.DSfile\shared_prefs\auto_login.pref.xml
This file contains the below
important information.
auto_login:
This field contains the status of auto login (true for enabled, false for
disabled).
auto_login_address: This field contains the NAS server address.
auto_login_account: This field contains the account used to login to NAS server.
XML File: SampleData\data\com.synology.DSfile\shared_prefs\com.google.android.gms.measurement.prefs.xml
This file contains the below
important information.
time_active:
Time app has been active in seconds.
has_been_opened: If application has been opened.
first_open_time: The first-time application was opened in epoch time.
app_install_time: The time application was installed in epoch time.
last_upload_attempt: Status of last upload attempt (0 for success).
last_upload:
The last time an upload was made in epoch time.
XML File: SampleData\data\com.synology.DSfile\shared_prefs\com.synology.DSfile_preferences.xml
This file contains the below
important information.
verify_cert_fingerprint: This field contains the status whether a certificate
must be verified on logon (true for enabled, false for disabled).
auto_login:
This field contains if auto login feature is active (true for enabled, false
for disabled).
XML File: SampleData\data\com.synology.DSfile\shared_prefs\connection_manager.xml
This file contains the below
important information.
userInput:
This field contains the NAS server path.
account:
This field contains the account used to logon.
Password:
This field contains the encrypted password used to logon.
url: This
field contains the NAS server path including the port.
isHttps:
This field contains if HTTPS is active (true for enabled, false for disabled).
XML File: SampleData\data\com.synology.DSfile\shared_prefs\DSFILE_PREFERENCE.xml
LOCAL_PATH:
This field contains the default path files get saved to when downloaded.
LAST_FOLDER:
This field contains the last local folder the app accessed.
last_addr:
This field contains the last server address the app connected to.
Cache Files:
SampleData\data\com.synology.DSfile\files\cache
The cache files directory
contains cache files in JSON format. Use the parse_cache_files.ps1 PowerShell
script to parse the cache files and export them to easy to read CSV files. The
SampleCSVs folder contains the output of the cache files in this sample. Fields
that contain timestamps (epoch time) are converted to Eastern Standard Time and
fields that contain size in bytes are converted to KB, MB, GB, TB, or PB.
The script and sample CSV files can be downloaded using the link located at the top of the page. Below are instructions for using the script. Below are instructions for using the script.
1.
Open PowerShell
as an Administrator
2.
Type the path of
the parse_cache_files.ps1 file and
press enter. If you get an error stating that “parse_cache_files.ps1 cannot be loaded because the execution of
scripts is disabled on this system”, then you must run “Set-ExecutionPolicy
RemoteSigned” first. After running the script, you will be prompted with the
below message box. Click Ok.
3.
Select the cache
files you want to parse. Keep in mind that the script will only look for
“.cache” extensions. You can select multiple cache files. After selecting the
cache files you want to parse, click Open.
4.
Next you will be
prompted with a message box stating to select the folder where you want to save
the parsed CSV files. Click OK.
5.
Select a folder
to save the parsed CSV files.
6.
Navigate to the
folder you selected. The parsed CSV files will contain the name of the cache
file including the extension.
Below are the outputs for the
sample cache files.
File: 6cb222e67c27fd2a7bd632f78c884233.cache
Description: This
cache file contains any file that was downloaded/emailed/shared.
Original Content
Parsed Content
File: 76265c2c38822202ef4edbac948a5eed.cache
Description:
This cache file contains favorite folders.
Original Content
Parsed Content
Description:
This cache file contains Shared Folder permissions.
Original Content
Parsed Content
File: ddcf4667fc9e8912cff15a62ba0d351c.cache
Description:
This cache file contains uploaded files.
Original Content
Parsed Content
File: f76c709095e91294161cdec441d833e2.cache
Description:
This cache file contains all files and folders at the root of the Shared
Folder.
Original Content
Parsed Content
File: fbf012134b179ce288c49efc5212c59d.cache
Description:
This cache file contains folders that have had a download/upload activity.
Original Content
Parsed Content
Conclusion:
DS File is a very popular NAS
app for Android that creates various artifacts that can determine the NAS it
connected to, the content on the NAS, and what actions were performed (download,
upload, etc). I hope this analysis, along with the script and sample data, can benefit
the mobile forensics community!































Comments
Post a Comment